INTRODUCTION TO LINUX CONTAINERS
Linux Containers have developed as an important open-source application packaging and delivery technology, combining lightweight application isolation with image-based deployment methods’ flexibility. RHEL implements Linux Containers leveraging fundamental technologies like Control Groups (Cgroups) for Resource Management, Namespaces for Process Isolation, and SELinux for Security, allowing secure multi-tenancy and lowering the risk of security attacks. All of this is intended to provide you with a setting in which you can create and run enterprise-quality containers.
Linux Containers Architecture
For Linux Containers to work properly, several components are required, the majority of which are provided by the Linux kernel. Process isolation is ensured via kernel namespaces, while system resources are managed by cgroups. The separation between the host and the container, as well as between the different containers, is ensured by SELinux. The management interface is a higher layer that interacts with the kernel components outlined above and provides tools for container building and management.
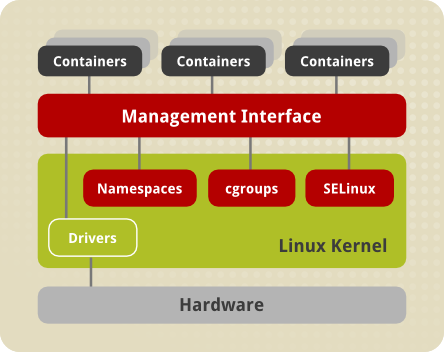
Namespaces
Separate namespaces for containers are created by the kernel to ensure process isolation. Namespaces allow you to abstract a specific global system resource and present it to processes within a namespace as a separate instance. As a result, many containers can consume the same resource at the same time without causing a conflict.
Containment Groups (cgroups)
Cgroups are used by the kernel to organize processes for system resource management. Cgroups distribute CPU time, system memory, network bandwidth, or a mix of these resources among user-defined task groups. Systemd slice, scope, and service units are used to handle cgroups in Red Hat Enterprise Linux 7.
SELinux
SELinux uses SELinux policy and labels to ensure secure container isolation. It uses the sVirt technology to integrate with virtual devices.
Image-based Containers
Containers based on images bundle applications with their runtime stacks, making them independent of the host operating system. This allows many instances of an application, each created for a separate platform, to operate simultaneously. Because the container runtime and the application runtime are both delivered as images, this is possible. For example, Runtime A may refer to Red Hat Enterprise Linux 6.5, while Runtime B may refer to Red Hat Enterprise Linux 6.6, and so on.
With image-based containers, you can host numerous instances and versions of an application with less overhead and more flexibility. These containers are portable since they are not connected to the host’s settings.
There are several RHCSA training in Kochi that can help you gain sufficient information on this subject. The best teachings and talents come from the best solutions courses. As a result, prepare for the future with the best RHCSA training in Kochi.